How do we configure Terraform and GCP to create resources in the Google cloud. You can also read this on the site of Hashicorp.
Make sure your GCP project is ready!
To use terraform on GCP, you have to create a project. This is easily done on the cloud console of GCP. I simply create a new project named “terraform-gcp“. The project ID stated is necessary to identify the project in your terraform script.
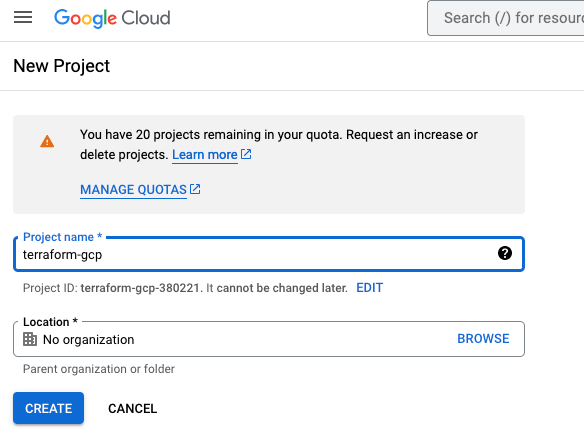
When the project is created, you have to enable certain features on your project. Just then, you can use terraform to deploy resources in GCP. For this intro for using Terraform on GCP, I enable the Compute Engine for this project. In your notifications, you can see the progress of enablement.
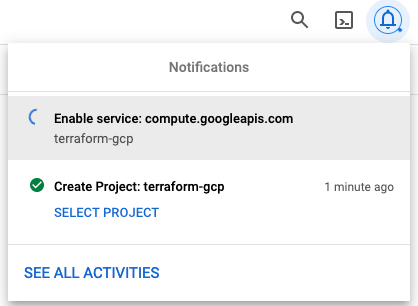
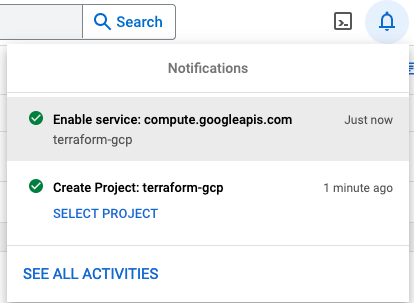
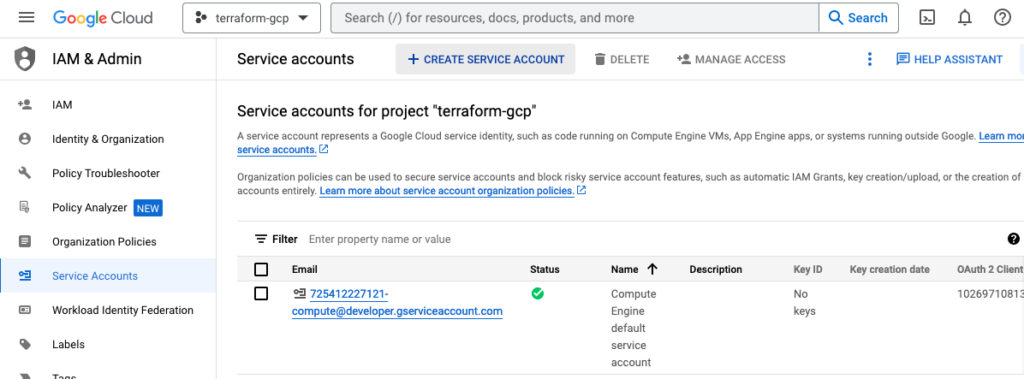
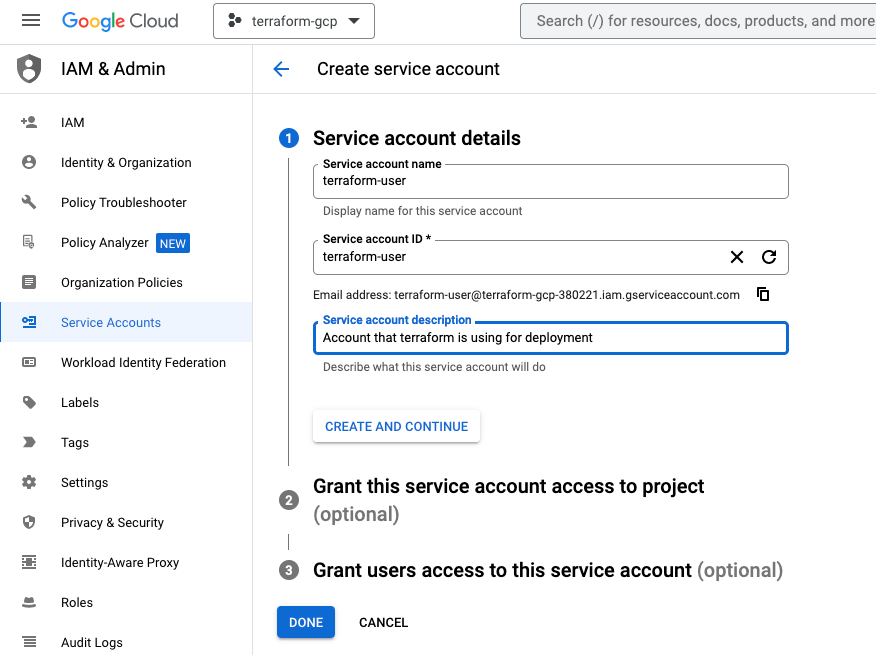
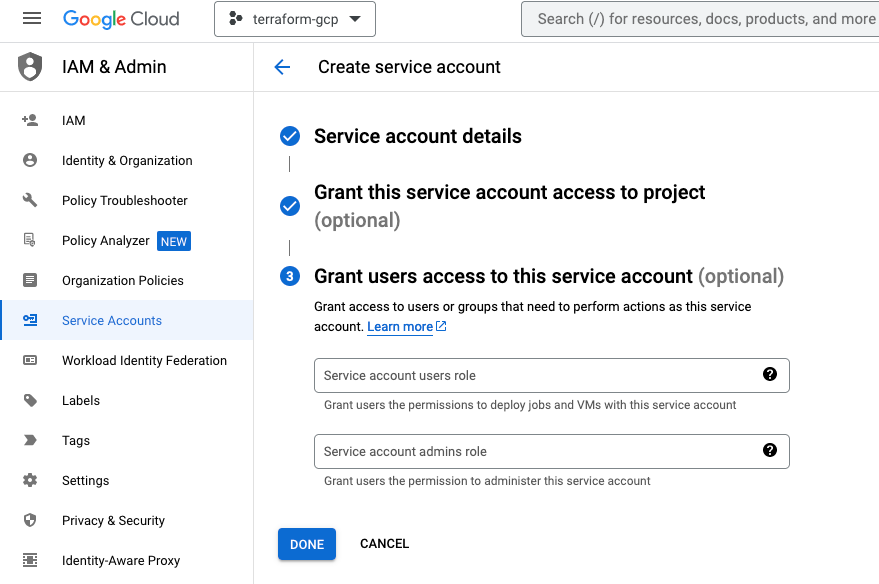
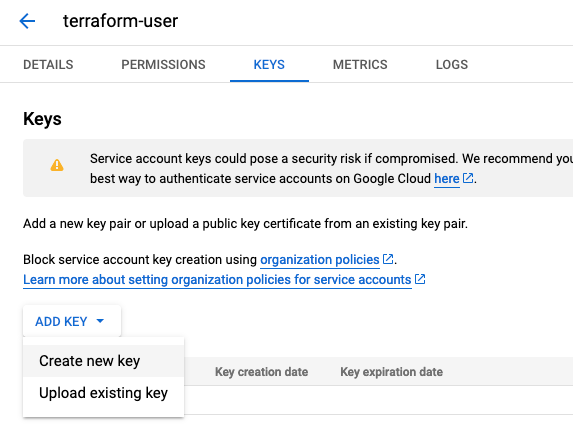
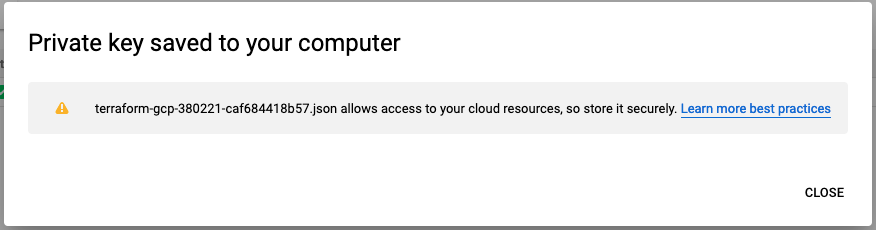
Finally in this preparation phase, you just have to create a service account with a corresponding key. During this process you provide a user role to the account and download the key to your desktop for further use.
Starting with Terraform
After this “preparation phase”, it is finally time to get started with Terraform… In a fresh folder you create a new main.tf file for your initial configuration. According to the hashicorp tutorial, I filled the file with the following information. I included information about the credentials. I also changed the reghion and zone. As a Dutchman, I would like to have my resources close to home.
terraform {
required_providers {
google = {
source = "hashicorp/google"
version = "4.51.0"
}
}
}
provider "google" {
credentials = file("terraform-gcp-380221-caf684418b57.json")
project = "terraform-gcp-380221"
region = "europe-west4"
zone = "europe-west4-a"
}
resource "google_compute_network" "vpc_network" {
name = "terraform-network"
After saving this main.tf, we are able to initiaze Terraform issuing the command “terraform init”.
Initializing Terraform
Issuing this command will make sure all necessary modules are installed on the system.
ubuntu@terraform:~/terraform-gcp$ terraform init Initializing the backend... Initializing provider plugins... - Finding hashicorp/google versions matching "4.51.0"... - Installing hashicorp/google v4.51.0... - Installed hashicorp/google v4.51.0 (signed by HashiCorp) Terraform has created a lock file .terraform.lock.hcl to record the provider selections it made above. Include this file in your version control repository so that Terraform can guarantee to make the same selections by default when you run "terraform init" in the future. Terraform has been successfully initialized! You may now begin working with Terraform. Try running "terraform plan" to see any changes that are required for your infrastructure. All Terraform commands should now work. If you ever set or change modules or backend configuration for Terraform, rerun this command to reinitialize your working directory. If you forget, other commands will detect it and remind you to do so if necessary.
Planning and deploying
When Terraform is initialized, you can proceed with planning and finally applying your infrastructure on GCP.
ubuntu@terraform:~/terraform-gcp$ terraform plan
Terraform used the selected providers to generate the following execution plan. Resource actions are indicated with the following
symbols:
+ create
Terraform will perform the following actions:
# google_compute_network.vpc_network will be created
+ resource "google_compute_network" "vpc_network" {
+ auto_create_subnetworks = true
+ delete_default_routes_on_create = false
+ gateway_ipv4 = (known after apply)
+ id = (known after apply)
+ internal_ipv6_range = (known after apply)
+ mtu = (known after apply)
+ name = "terraform-network"
+ project = (known after apply)
+ routing_mode = (known after apply)
+ self_link = (known after apply)
}
Plan: 1 to add, 0 to change, 0 to destroy.
───────────────────────────────────────────────────────────────────────────────────────────────────────────
Note: You didn't use the -out option to save this plan, so Terraform can't guarantee to take exactly these actions if you run
"terraform apply" now.
When the output of the planning is as expected, you can proceed with applying this configuration. Just issue the command “terraform apply”. Just enter “yes” to confirm.
ubuntu@terraform:~/terraform-gcp$ terraform apply
Terraform used the selected providers to generate the following execution plan. Resource actions are indicated with the following
symbols:
+ create
Terraform will perform the following actions:
# google_compute_network.vpc_network will be created
+ resource "google_compute_network" "vpc_network" {
+ auto_create_subnetworks = true
+ delete_default_routes_on_create = false
+ gateway_ipv4 = (known after apply)
+ id = (known after apply)
+ internal_ipv6_range = (known after apply)
+ mtu = (known after apply)
+ name = "terraform-network"
+ project = (known after apply)
+ routing_mode = (known after apply)
+ self_link = (known after apply)
}
Plan: 1 to add, 0 to change, 0 to destroy.
Do you want to perform these actions?
Terraform will perform the actions described above.
Only 'yes' will be accepted to approve.
Enter a value: yes
google_compute_network.vpc_network: Creating...
google_compute_network.vpc_network: Still creating... [10s elapsed]
google_compute_network.vpc_network: Still creating... [20s elapsed]
google_compute_network.vpc_network: Still creating... [30s elapsed]
google_compute_network.vpc_network: Still creating... [40s elapsed]
google_compute_network.vpc_network: Still creating... [50s elapsed]
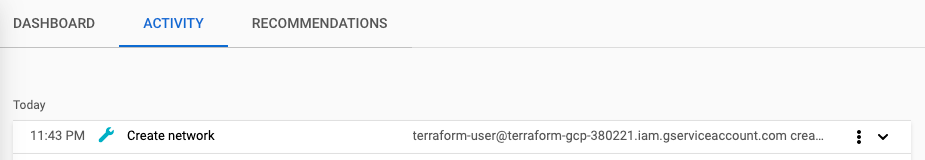
google_compute_network.vpc_network: Creation complete after 53s [id=projects/terraform-gcp-380221/global/networks/terraform-network]
Apply complete! Resources: 1 added, 0 changed, 0 destroyed.
ubuntu@terraform:~/terraform-gcp$
Final thoughts
As you can see in this post, and on the Hashicorp site, it is quite simple to start with terraform on the Google Cloud Platform. This is not unique to GCP, but also is simple for AWS and Azure as well.
Next question, how to make sure your providers are up-to-date and still usuable? That, and more to come!
Leave a Reply