Information about Nutanix Kubernetes Platform (Part 7 of many)
Platform applications are almost essential for good and proactive management of containerized workloads. Many functions are performed by this platform applications, such as collecting logs, monitoring metrics, as well as providing visualization and performing back-up and restore. The post gives an overview of the applications that are used by the Nutanix Kubernetes Platform.
More information can be found on the section ‘Platform Applications‘ in the NKP documentation on the Nutanix portal.
Default foundational applications
Default foundational applications provide the basis fort the application capabilities and deployments on managed clusters. The applications must be enabled for any platform application to work properly.
The default applications are Cert-Manager, Reloader, Traefik and Chart Museum. Although they are enabled on the cluster, not all applications are shown in the UI. Using the CLI command ‘kubectl get helmreleases‘, they can be viewed.
| Default Platform Application | Purpose |
|---|---|
| Cert-Manager | Cert-Manager automates Transport Layer Security (TLS) certificate management and issuance. The certificates issued by cert-manager are from certificate authorities that include Let’s Encrypt, HashiCorp Vault, Venafi, private PKI, and so on. |
| Reloader | Reloader is a controller that watches for changes to configmaps and secrets, and automatically triggers updates on dependent applications. |
| Traefik | Traefik allows ingress into a cluster and provides an HTTP reverse proxy and load balancer. This application requires cert-manager and reloader. |
| Chart Museum | Chart Museum is an open source Helm chart repository that contains a collection of files that describe a set of Kubernetes resources. Chart Museum is used on air-gapped installations to store Helm charts. In non-air-gapped installations, charts are fetched from upstream repositories and Chart Museum is not installed. |
Click on the Application to be redirected to the official documentation.
Logging Applications
Logging applications collect logs over time from Kubernetes and applications deployed on managed clusters. They allow you to visualize and query aggregated logs. By default, the logging stack is NOT deployed. You are able to see the logging applications in the UI.
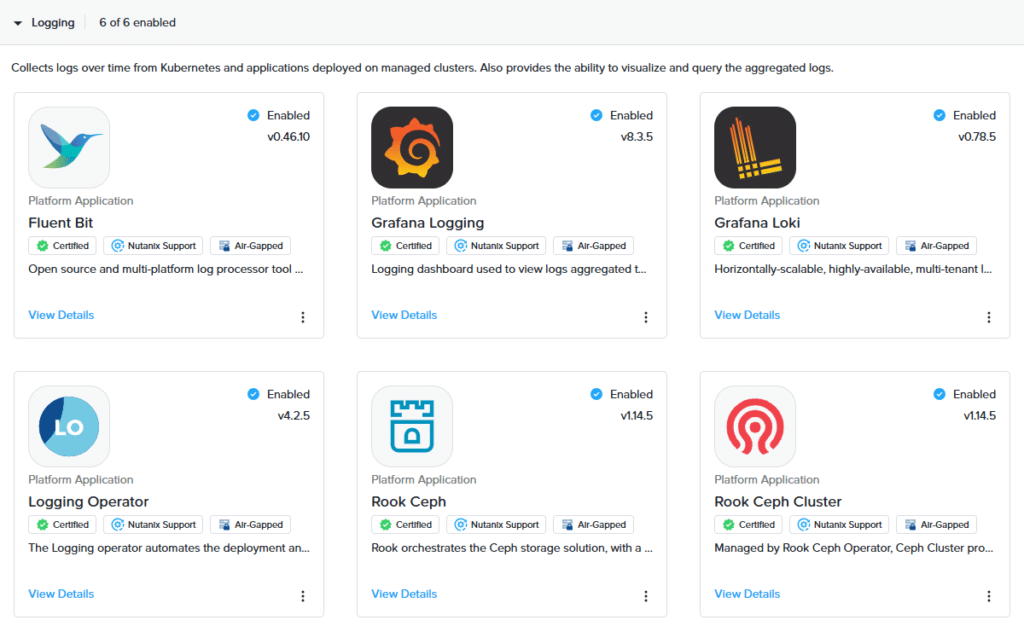
| Logging applications | Purpose |
|---|---|
| Fluent Bit | Fluent Bit is an open source, multi-platform log processor tool that collects and processes data from different sources and can be used for tasks such as log processing and distribution. |
| Grafana | Grafana collects metrics and provides data visualization and monitoring capabilities. You can use Grafana to query data, create dashboards, explore metrics, scan logs, and more. Grafana consists of the grafana-logging and the grafana-loki application. Grafana Loki requires the installation of Rook Ceph Cluster. |
| Logging Operator | Logging Operator is a log aggregation system that automates the deployment and configuration of a Kubernetes logging pipeline. |
| Rook Ceph | Rook is an open source tool that automates the deployment and management of Ceph storage (file, block, and object) in your Kubernetes cluster. |
| Rook Ceph Cluster | A Rook Ceph Cluster is a Kubernetes-native high-performance object store with an S3-compatible API that supports deployment into private and public cloud infrastructures. |
Monitoring Applications
Monitoring applications are collecting metrics, provide visualization and evaluate rule expressions, so alerts can be triggered when specific conditions are met. The monitoring stack is deployed by default.
| Monitoring Application | Purpose |
|---|---|
| Kubecost | Kubecost provides real-time cost visibility and insights for teams using Kubernetes and helps reduce your cloud costs. |
| Kubernetes Dashboard | The Kubernetes Dashboard is a general-purpose, web-based UI for Kubernetes clusters. You can use it to monitor and manage cluster resources, and deploy, manage, and troubleshoot applications on your clusters. |
| Kube Prometheus Stack | The Kube Prometheus Stack is a stack of applications that collect metrics and provide visualization and alerting capabilities. |
| Nvidia GPU Operator | The NVIDIA GPU Operator manages NVIDIA GPU resources in a Kubernetes cluster and automates tasks related to bootstrapping GPU nodes. |
| Prometheus Adapter | The Prometheus Adapter provides cluster metrics from Prometheus. |
Security Applications
Security applications allow management of security constraints and capabilities for clusters and users.
| Security Applications | Purpose |
|---|---|
| Gatekeeper | Gatekeeper is a policy controller for Kubernetes that enforces CRD-based policies executed by Open Policy Agent (OPA). |
Single Sign On Applications
Single Sign On (SSO) ia a centralized authentication system that connects attached clusters to the centralized authority on the management cluster. This allows users to access multiple applications with a single credential. SSO applications are a group of platform applications that allow you to enable SSO on attached clusters.
| SSO Applications | Purpose |
|---|---|
| Kube OIDC Proxy | Kube OpenID Connect (OIDC) Proxy is a reverse proxy server that authenticates users using OIDC to Kubernetes API servers where OIDC authentication is not available. |
| Traefik ForwardAuth | Traefik ForwardAuth installs a forward authentication application providing Google OAuth based authentication for Traefik. |
Backup Applications
In production environments backup can be very useful. Data should ever be protected. Backup applications allow you to back-up and restore your envirinment.
| Backup Applications | Purpose |
|---|---|
| Velero | Velero is an open source tool used to safely back up and restore resources in a Kubernetes cluster, perform disaster recovery, and migrate resources and persistent volumes to another Kubernetes cluster. |
Platform Applications Dependencies
When (Platform) applications are interacting with eachother, it could be that applications are depending on other applications. When you are going to customize platform applications, it can be helpful to be aware of the dependencies. If dependencies are not met, applications are not deployed properly.
Some examples of dependencies are already mentioned before.
- Foundation application Traefik requires Cert-Manager and Reloader.
- Logging application Grafana Logging requires Grafana Loki. Grafana Loki requires Rook Ceph Cluster.
- Monitoring application Prometheus Adapter requires Kube Prometheus Stack.
For example, when a Velero backup is performed, the backup is stored in a bucket which is created inside Rook Ceph Cluster and hence Velero’s dependency on Rook Ceph Cluster.
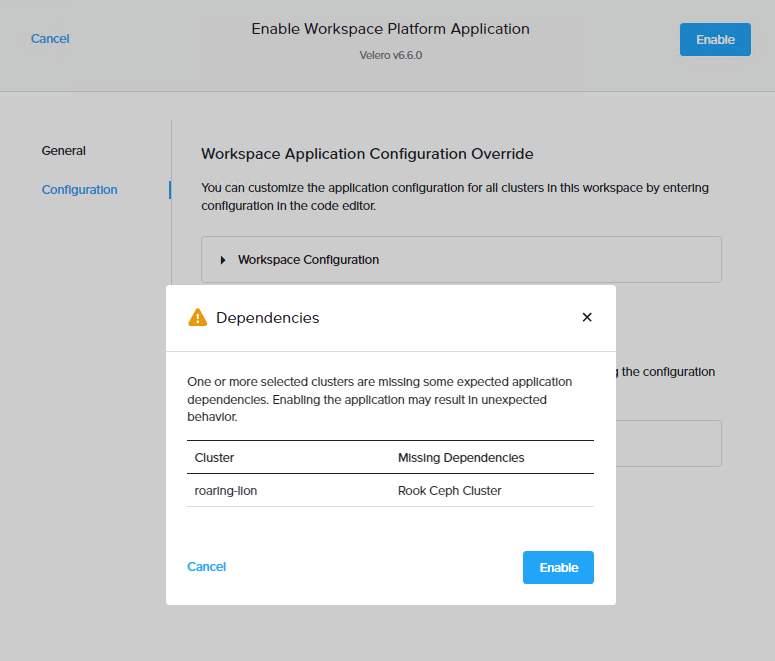
Before enabling Velero backup platform application, Rook Ceph Cluster platform application must be enabled. If not enabled, the application will result in an unexpected behavior, as shown in the adjacent figure.
Note that NKP identifies other Platform Application dependencies and will provide a dependency warning before allowing the application to be enabled if they are not met.
For a complete list of platform application dependencies, see the Platform Applications Dependencies section of the Nutanix Kubernetes Platform Guide.
Resource Requirements
Some applications are installed by default. Other applications you have to install manually. When deploying or attaching clusters you have to make sure that your clusters do have resources available for the platform services to be installed.
For resource requirements, visit the Workspace Platform Application Defaults and Resource Requirements page. In this post a few examples are shown.
| Common Name | App ID | Deployed by default | minimum resources | Minimum persistent storage | Default Priority Class |
|---|---|---|---|---|---|
| Cert Manager | cert-manager | Yes | cpu: 10m memory: 32Mi | system-cluster-critical | |
| Fluent Bit | fluent-bit | No | cpu: 350m memory: 350Mi | NKP Critical | |
| Gatekeeper | gatekeeper | Yes | cpu: 300m memory: 768Mi | system-cluster-critical | |
| Grafana | grafana-logging | No | cpu: 200m memory: 100Mi | NKP Critical | |
| Loki | grafana-loki | No | # of PVs: 8 PV sizes: 10Gi | NKP Ciritical | |
| Velero | velero | No | cpu: 1000m memory: 1024Mi | NKP Critical |
- Currently, NKP only supports a single deployment of Cert-Manager per cluster. Because of this, Cert-Manager cannot be installed on any Konvoy managed clusters or clusters with Cert-Manager pre-installed.
- Only a single deployment of Traefik per cluster is supported.
- NKP automatically manages the deployment of Traefik ForwardAuth and Kube OIDC Proxy when clusters are attached to a workspace. These applications are not shown in the NKP UI.
Reviewing deployed platform applications
Before starting deploying platform applications, you should always review currently installed applications. By doing this, you can check if dependencies are met.
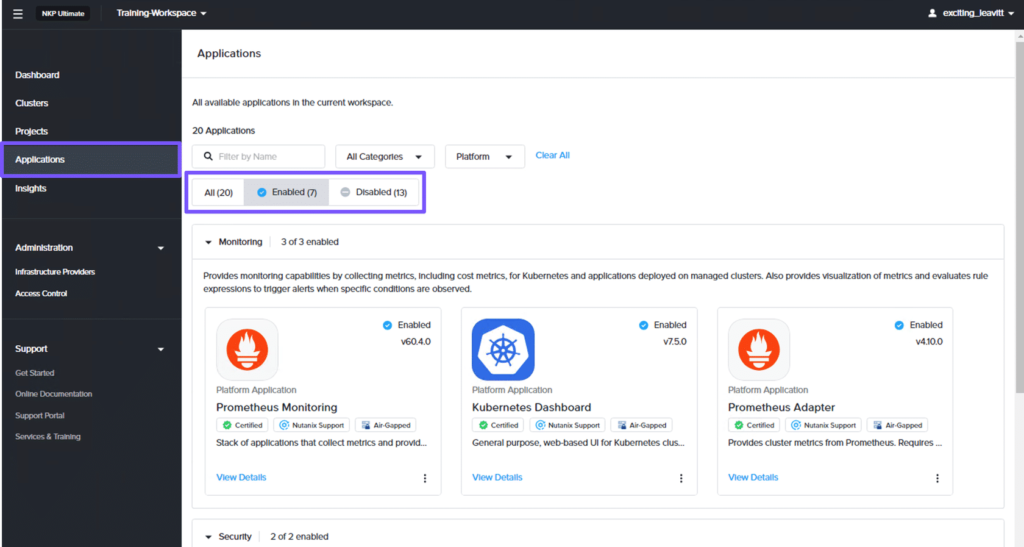
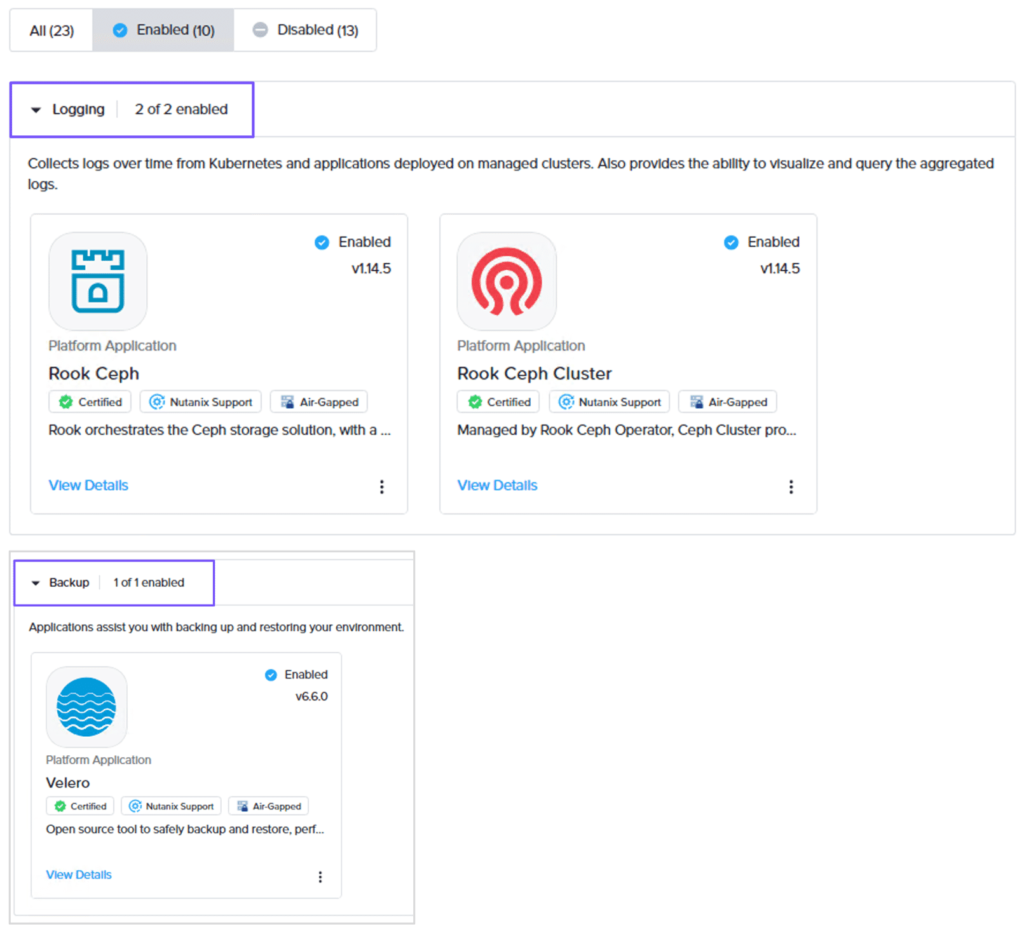
To review the default platform applications, on the workspace dashboard, select Applications from the left pane. On the Applications page, select Enabled to review all the applications that have been enabled in the workspace.
Note that only three categories of platform applications have been enabled in the workspace.
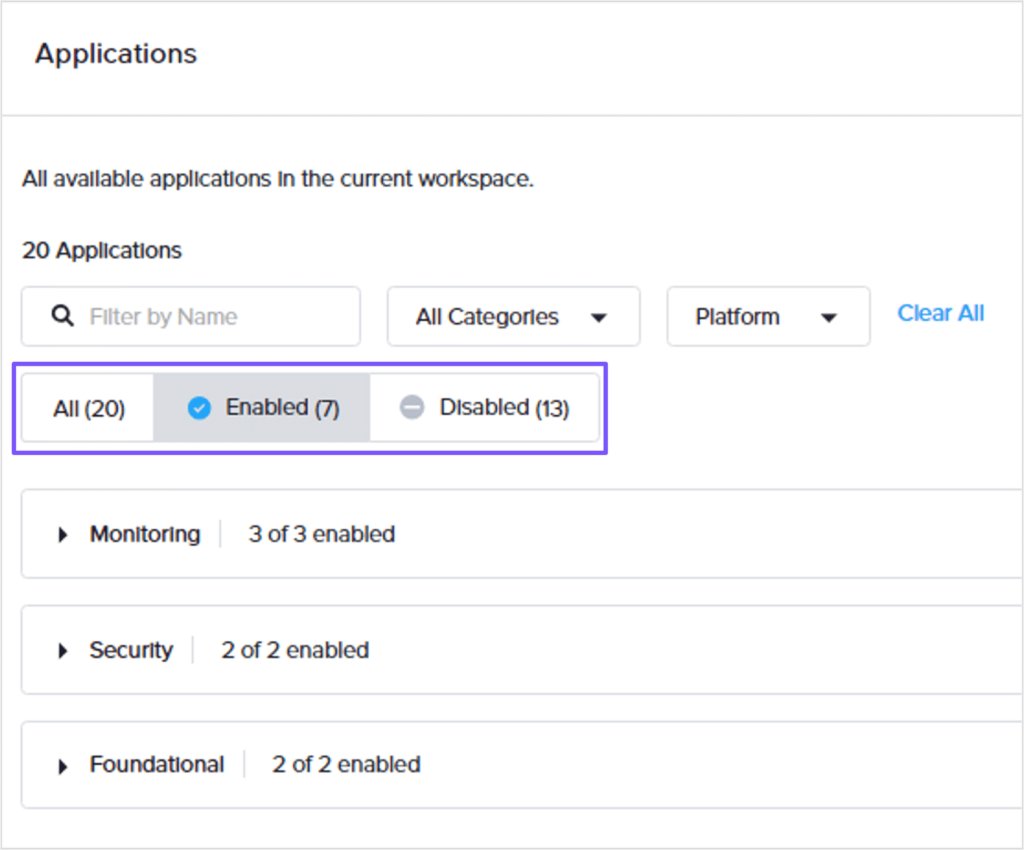
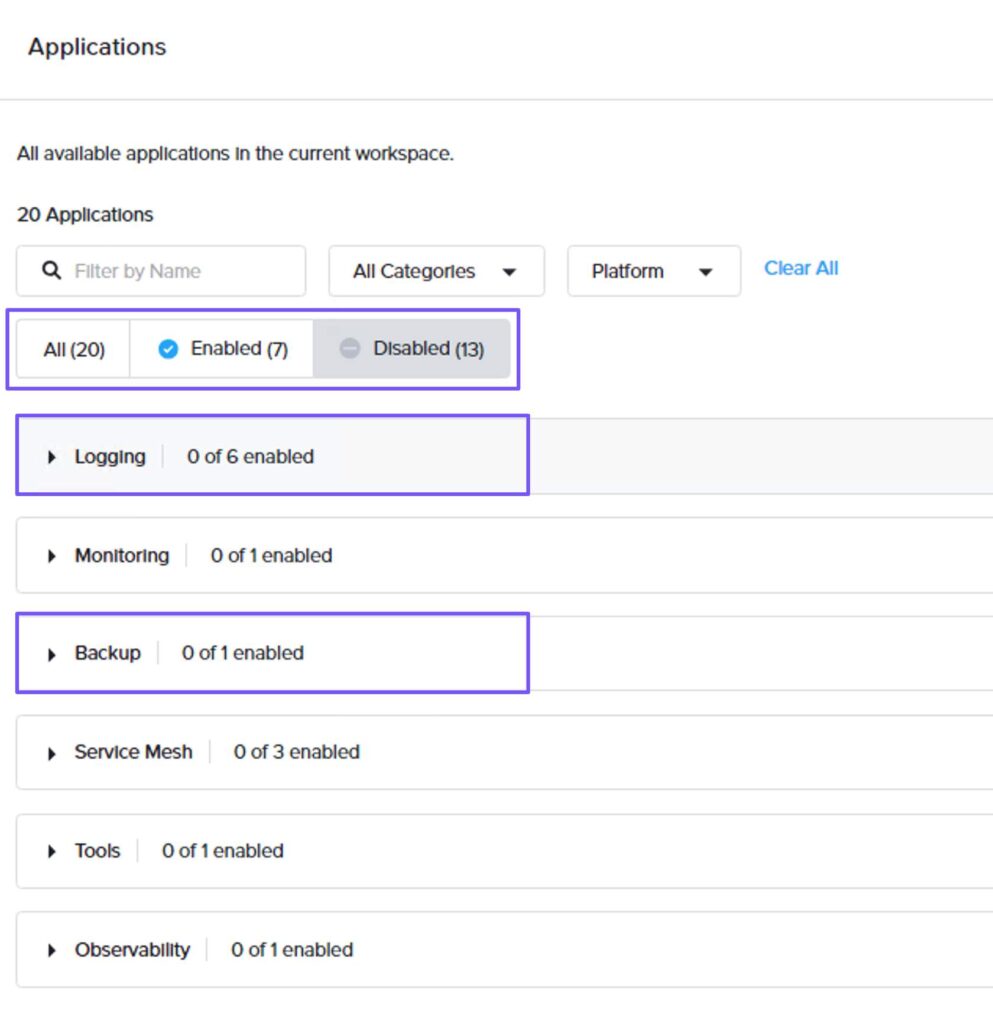
Then, click Disabled to review all the disabled applications in the workspace. Note that Logging and Backup platform applications are Disabled by default.
Deploying Platform Applications
In a few steps Platform applications can be deployed.
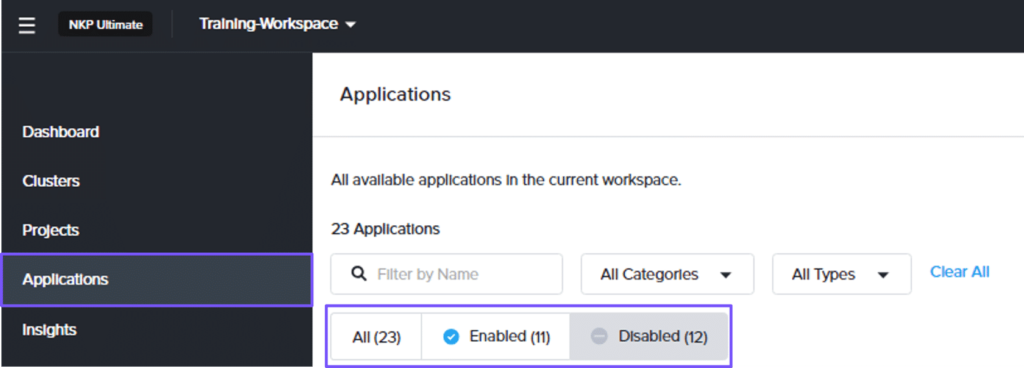
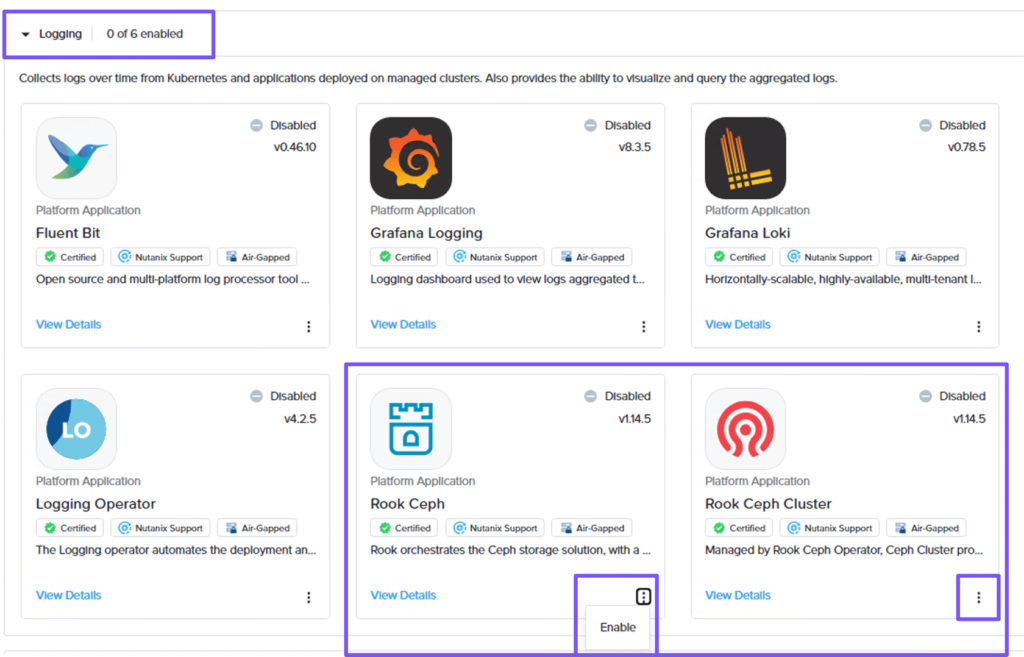
To deploy Logging platform applications, in the workspace dashboard, select Applications from the left pane. On the Applications page, select Disabled.
In the Logging category, click the ellipses for the Rook Ceph and Rook Ceph Cluster widgets and click Enable.
Rook Ceph Cluster has an application dependency on Rook Ceph so, in this example, we are enabling both applications. Then, we will enable Velero backup application which has an application dependency on Rook Ceph Cluster.
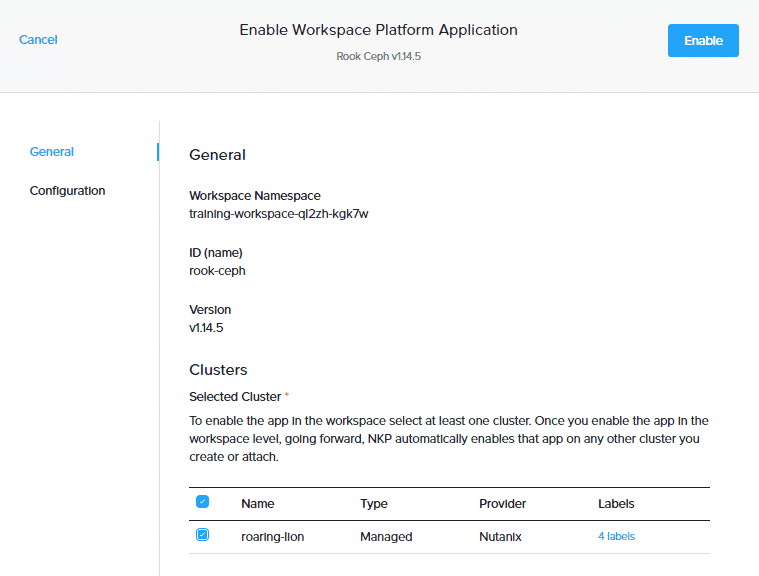
On the Enable Workspace Platform Application page, in the General step, select the cluster in the Clusters section to enable the app in the workspace. Enabling an app at the workspace level will automatically enable it on other clusters created or attached to this workspace in the future.
In the Configuration step, you can customize the application configuration individually for each cluster or at once for all clusters in this workspace. In this example, we will leave the default settings and click Enable.
Now that Rook Ceph has been enabled, you can repeat the same steps to enable Rook Ceph Cluster platform application.
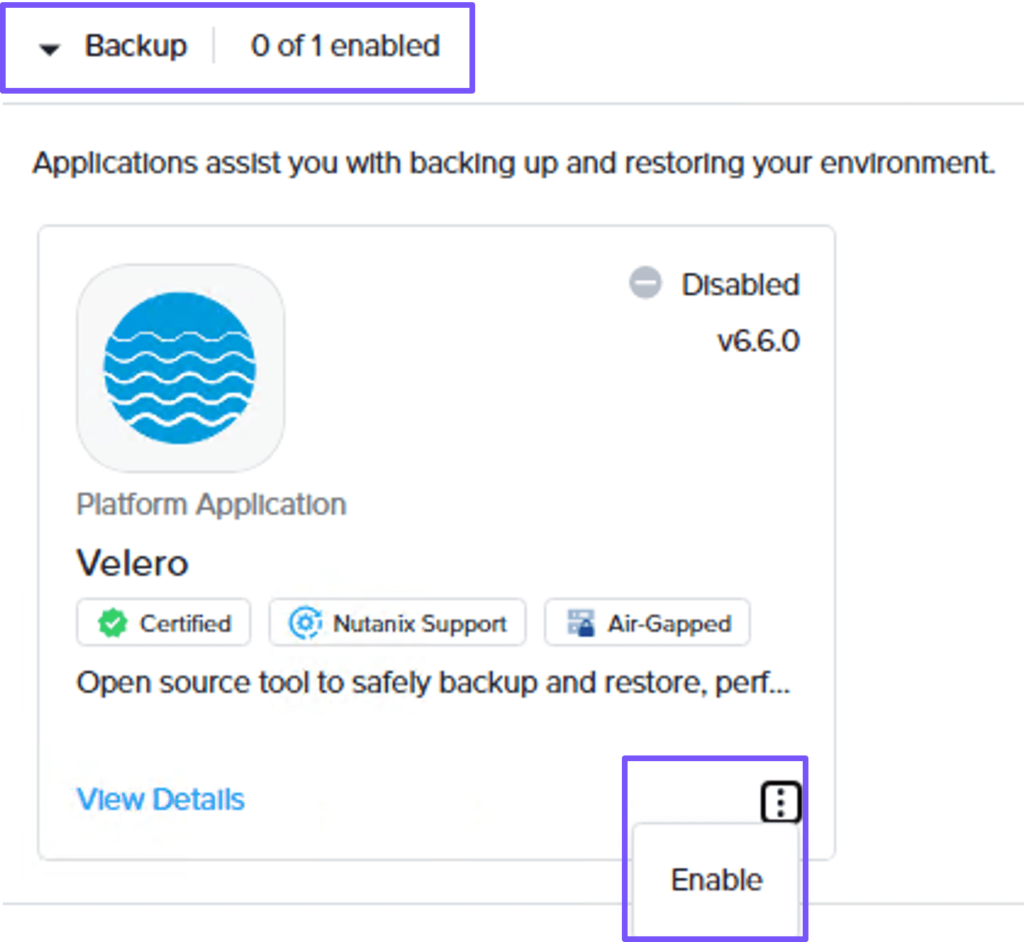
Next, to deploy a Backup platform application, on the Applications page, select Disabled. In the Backup category, click the ellipses in the Velero widget, and click Enable.
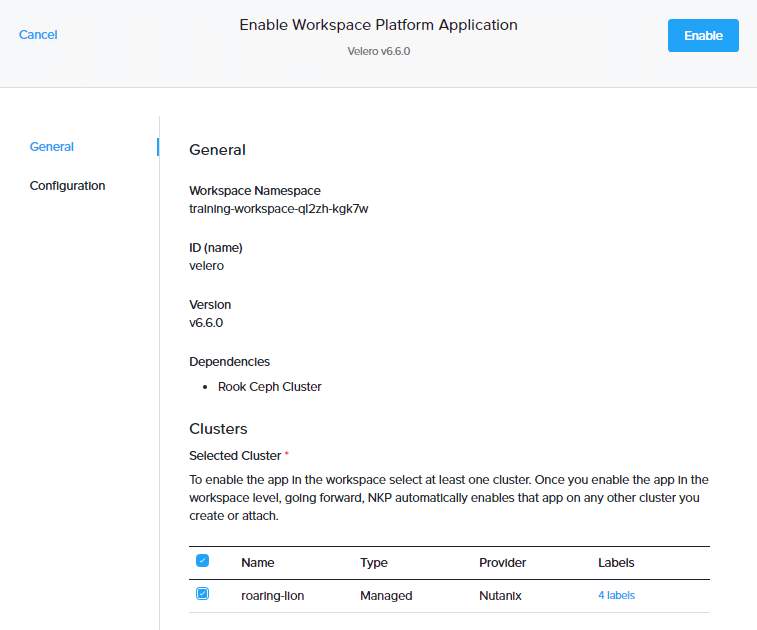
On the Enable Workspace Platform Application page, in the General step, select one or more clusters on which to enable the app. Selecting at least one cluster will enable the app at the workspace level. This, in turn, will automatically enable this app on other clusters created or attached to this workspace in the future.
In the Configuration step, you can customize the application configuration individually for each cluster or at once for all clusters in this workspace. In this example, we will leave the default settings and click Enable.
Now that we have enabled our Logging and Backup platform applications, they will appear on the Applications page under Enabled applications.
Leave a Reply